Industries
Good to know
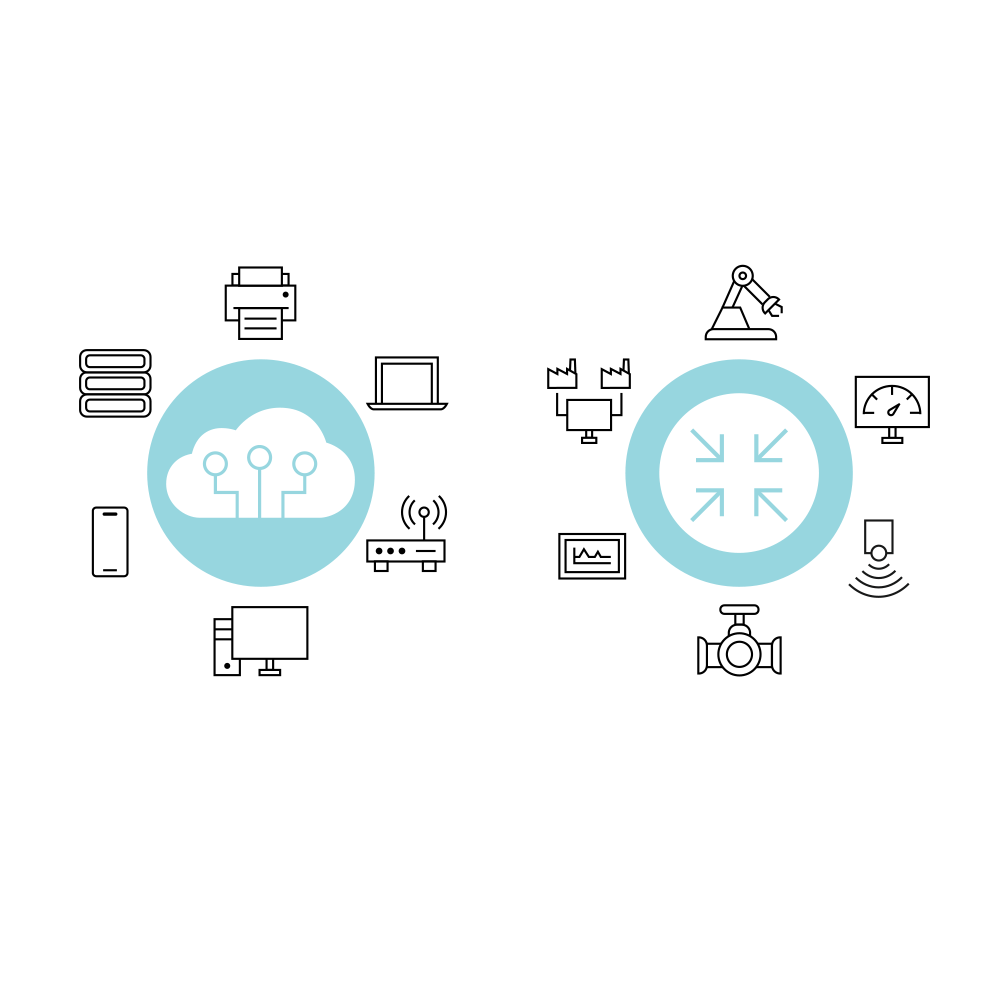
Where IT and OT converge
IT is the digital brain – managing data, communication and business applications. OT is the muscle behind the machines. It controls compressors, sensors and industrial processes in real time. For decades these two domains operated independently, but today they are increasingly connected: Machine-generated data from OT systems flows into IT platforms for advanced analytics, while IT tools simultaneously access OT environments for real-time monitoring and operational insights. This convergence enables smarter and more efficient operations but also increases the risk of cyber attacks. A unified and robust cyber security strategy that spans both IT and OT is therefore essential to protect everything from compressor sensors to cloud access and ensure resilient operations.
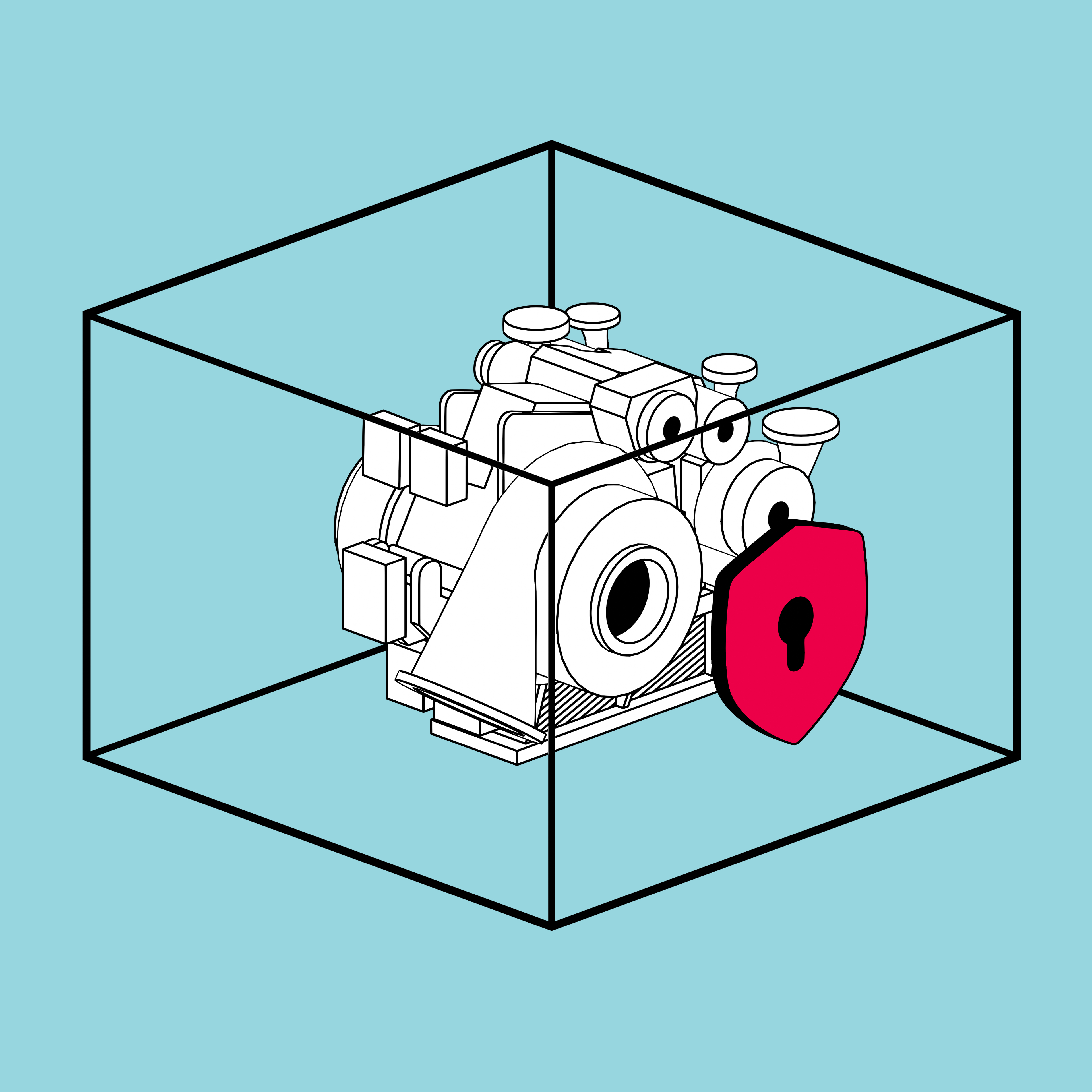
Robust OT security for critical operations
We secure your industrial units from control components to networks and processes, fully aligned with IEC 62443, ISO 27001 and, where applicable, local compliance and governance requirements.
Following our proven “Defense in depth” concept, we layer security measures to protect every level of your operation. We begin with precise requirement analysis, apply system hardening with integrated safeguards, and finish with thorough validation. The result: Threat resilience, operational continuity, and long-term protection – delivering maximum availability, minimal risk, and proven compliance.
Everllence
What our experts have to say
By loading the video you agree to YouTube's privacy policy.
Our approach: Defense in depth


Autonomous operations
Autonomous operation in turbomachinery is rapidly evolving, driven by digital innovations and cross-industry expertise. Everllence outlines a strategic roadmap toward fully unmanned, energy-efficient systems by 2028, supported by AI, digital twins, and remote services.


“Minimize risk, maximize availability – security is not an option, it’s a necessity for your turbomachinery.”
Dr. Khyati Shukla, OT Cyber Security Lead, Everllence
Upcoming events
.png?sfvrsn=ae246299_1)
Digitalization
This might also interest you
Downloads
Continue reading






Need guidance?
Speak with our cyber security experts today
Our experts are here to help you assess risks, close security gaps, and find the right solution – from on-premises protection to secure remote access.